Deep Human Super Skills for a VUCA world
We live in a world dominated by volatility, uncertainty, complexity and ambiguity (VUCA). Our traditional approach to a working career, learning a specific skill and stick to it, doesn't fit anymore. What is needed instead, is the subject of the book Deep Human writen by Crystal Lim-Lange and Dr. Gregor Lim-Lange.
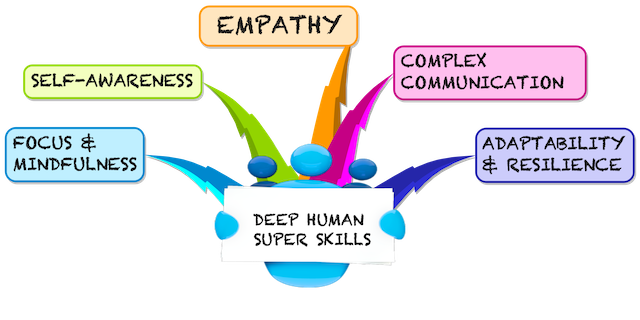
5 skills
The 5 skills build on each other, forming the foundation and prerequisite for the next level. Here is my take, paraphrasing what I learned, how they fit together. Full details, including experiences how to get there are in the book.
-
Mindfulness Being rooted in reality, seeing what is, without judgment and deep filters is the foundation of any progress. The practise of precisely observing your suroundings allows you to gather evidence for any assessment and action. The mindful person is master of their thoughs and doesn't fall prey easily to illusions. Of course it takes lifelong practise. The mind is like a muscle: once you start or stop training, it changes
-
Self-Awarness Once the mind has been sharpened and silenced, you can turn attention to the self. What are the sensations, emotions, thoughts, fears, hopes and believes that drive you? Armed with focus and mindfulness you can wrestle the driver's seat back from the monkey mind. Clarity about yourself leads to freedom to decide who you want to be instead of running on auto-pilot
-
Empathy Having honed the skill of self-awareness you can apply that to other sentients. Without clarity about yourself, this would fail, so self-awareness is the foundation of empathy, as mindfulness is the foundation of self-awareness. Learning to walk in someone elses shoes deepends your understanding of a complex world. Empathy isn't a woolsy-shoolsy be nice to everybody feeling, but the application of reality from a different viewpoint. As the late Lama Marut would say: "Be nice and don't take shit"
-
Complex communication You are able to see things as they are, you recognise strength and weaknesses in yourself and others. You value reality over opinions and solutions over debate. Skilled like this, explaining the not-so-simple, cutting to the chase, getting your point across becomes your next level. You won't get there without the foundation of Empathy, Self-Awareness and Mindfulness
-
Resillience and Adaptability Life changes, subtle or sudden, minimal or radical. You have practised to communicate clearly, see reality from different perspectives as it is and know yourself. These skills and the resulting confidence enables you to face whatever comes your way. Not clinging to illusions makes you flexible like the bamboo in the wind. You will clearly see what is needed and where you can find purpose. You adapt.
The whole book is an insightful and interesting read, so go and get your copy.
Posted by Stephan H Wissel on 27 October 2019 | Comments (0) | categories: After Hours Singapore