IE6 must die!

Posted by Stephan H Wissel on 28 March 2011 | Comments (1) | categories: Software
Usability - Productivity - Business - The web - Singapore & Twins

Posted by Stephan H Wissel on 28 March 2011 | Comments (1) | categories: Software

Posted by Stephan H Wissel on 27 March 2011 | Comments (1) | categories: Singapore
Posted by Stephan H Wissel on 27 March 2011 | Comments (2) | categories: Show-N-Tell Thursday
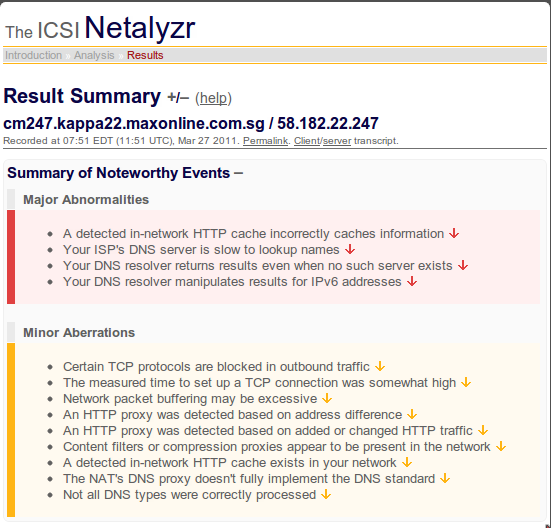
Posted by Stephan H Wissel on 27 March 2011 | Comments (5) | categories: Singapore Technology

Posted by Stephan H Wissel on 20 March 2011 | Comments (0) | categories: After hours

Posted by Stephan H Wissel on 19 March 2011 | Comments (0) | categories: After hours
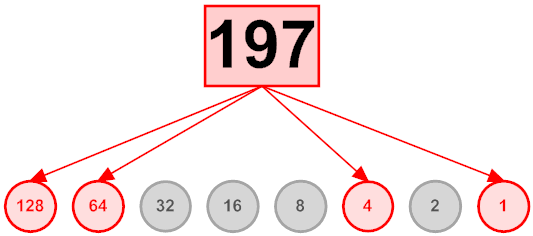
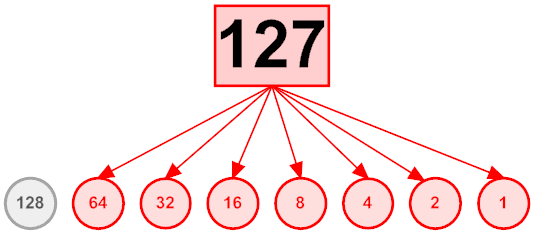
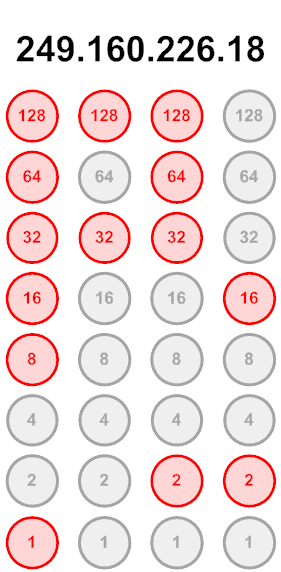
Posted by Stephan H Wissel on 19 March 2011 | Comments (0) | categories: Software
Posted by Stephan H Wissel on 19 March 2011 | Comments (6) | categories: After hours
compact -c is part of your database hygiene routines.
[Wherever-contig-is]\contig -a -s [Path-to-Domino-data-directory]\*.nsf > fragmentation.txt If you have database or directory links you have to repeat the process but then you need >> fragmentation.txt. This will list out the files and their fragmentation. Don't forget the -a parameter that tells contig to list only and not to actually defragPosted by Stephan H Wissel on 14 March 2011 | Comments (9) | categories: Show-N-Tell Thursday
Posted by Stephan H Wissel on 10 March 2011 | Comments (0) | categories: Show-N-Tell Thursday
Posted by Stephan H Wissel on 07 March 2011 | Comments (1) | categories: Show-N-Tell Thursday
isManager or isConfidential (Important: that are FIELD names, so no quotes). I like using "is" as prefix since the keyword describes a state of the document and based on that state information is supposed to be shown or hidden. De facto you create your domain specific language here. Now you create one computed for display (CfD) numeric field with exactly that name, so you have fields named isManager or isConfidential. That fields need to have results that are either @True or @False. To get to that result you can use anything at your disposal including profile documents or <gasp>@DBLookup or @DBColumn</gasp>. You could allow simple AND or OR statements like isDraft | !isManagerHaving done that you can start thinking about reuse.
"isManager":"isDraft" (Note: you have quotes here!). On a subform you would have a CfD field HideWhen_[Name of the subform]. When you add a subform you would adjust the HideWhenUsedHere formula to look like @Trim(@Unique("isManager":"isDraft":HideWhen_[Name of the subform])). Then add to the first line of each CfD field of your hidewhen-subform: @if(@IsNotMember(@ThisName;HideWhenUsedHere);@Return(@False);""); This way your eventual longer running lookup won't execute. The @isMember executes very fast. Of course you could construct it the other way around and have a field " DoNotUseTheseHideWhenHere", then the first line would look like this: @if(@IsMember(@ThisName;DoNotUseTheseHideWhenHere);@Return(@False);"");
Posted by Stephan H Wissel on 07 March 2011 | Comments (1) | categories: Show-N-Tell Thursday
CREATE TABLE statements you use to create your RDBMS tables and views. Advantage of SQL DDL is its closeness to RDBMS, which makes implementing the described data easy, the ability to create the definition in a simple text editor but also rich visual tools (like ERwin which was one of the first of its kind) and the capablity of other DDL (like UML) to read/write SQL DDL. The biggest drawback in a world where SQL no longer rules alone is its closeness to RDBMS and its lack of support for transmittable data (think web service, sync or two folded MVC pattern). Today I would say SQL DDL is hardly the source of your data model anymore, but an output from one of the other DDLs (most likely UML)Posted by Stephan H Wissel on 06 March 2011 | Comments (2) | categories: Show-N-Tell Thursday Software XPages
Posted by Stephan H Wissel on 06 March 2011 | Comments (0) | categories: After hours